Ensuring the privacy and protection of respondent data is our utmost priority. At Laterite, we collect sensitive information on topics from education to unplanned settlements to gender-based violence to make sure our clients and partners can make decisions based on rigorous evidence. In addition to complying with legal regulations and professional and ethical codes of conduct, we have a responsibility to protect the privacy of respondents who trust us with sensitive information.
In 2019, Laterite collected data from over 30,000 respondents and spent over 10,000 days in the field in Rwanda alone. A typical data collection project at Laterite has on average 1,000 respondents and a survey length of approximately one hour. That’s a lot of data to protect.
How do we collect respondent data?
We code our surveys electronically on SurveyCTO, the platform we use to collect respondent data. Our enumerators then use mobile devices such as tablets and mobile phones to collect data from respondents in both face-to-face and phone surveys.
For particularly sensitive subjects, we use data collection methods that guarantee respondent privacy, such as audio computer-assisted self-interviewing (ACASI). ACASI allows respondents to listen to pre-recorded survey questions and record their responses directly.
In addition, we follow the principle of data minimization. This means we collect only the information needed to answer the research question for each study.
Protecting data at every step of the process
It’s important to secure respondent data at every point in the process: from the mobile collection device, to the cloud server, to our internal server, to employee laptops. If data is not properly protected, it can be exposed to threats such as unauthorized access, data breaches, or data corruption and loss. From collecting data on the mobile device to sharing it with clients, we follow several data security principles to keep respondent data safe.
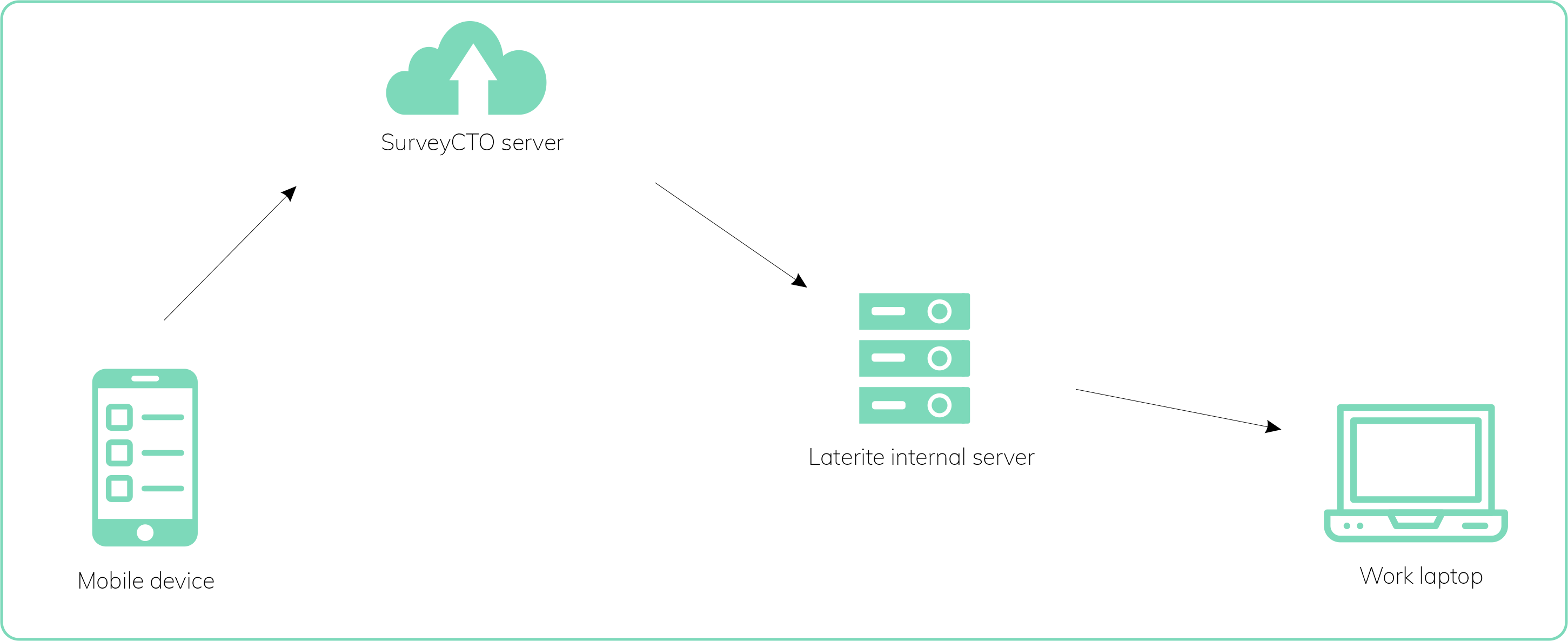
The flow of respondent data at Laterite Rwanda
Access control
A big advantage of electronic data collection is the ability to use secure digital methods to protect data. That being said, loss or theft of devices could lead to unauthorized access if not managed properly.
During fieldwork projects, we ensure that tablets remain at all times under the control of the field team. Laterite staff access data on their work laptops via a secure connection, either through the local area network or an encrypted network when working from home.
Wherever possible, our staff work with de-identified datasets. This minimizes exposure of a respondent’s personally identifiable information in case of unauthorized access. Our staff are able to carry out most cleaning and analysis tasks successfully without this information.
Data encryption
Encryption is the next step in preventing unauthorized access to data or data breaches. SurveyCTO encrypts all survey data at rest on the mobile device, which means that the data can only be read with a private decryption key. Only members of Laterite’s management team working on the project have this key.
Once interviews are finalized each day, enumerators upload the data from the mobile device to SurveyCTO’s cloud server. At this point, the data is encrypted in transmission and at rest, preventing unauthorized access. Once the data has been transferred to the cloud server, it is erased from the mobile device. This data is then transferred from the cloud server to Laterite’s internal server each day, from which staff can access it.
We use full disk encryption on our internal Laterite server as well as all company laptops. This makes the data unreadable without a decryption key, protecting it from possible data breaches.
Back-ups and secure data transfer
A third step we take to protect our data is to back it up at key points. SurveyCTO backs up data when it reaches the cloud server. We also back up all data on our Laterite server to a secure remote server daily.
When working with raw data, we work with read-only datasets, which prevents staff accidentally corrupting or over-writing the data. We also routinely update all data storage systems and applications with the latest security patches.
Finally, we take care to make sure that our clients receive the data securely. We use secure file sharing services which encrypt files at rest and enable access control, such as Dropbox and Google Drive or via an SFTP (Secure File Transfer Protocol) server. We never share respondent contact details with clients unless strictly necessary for the continuity of the project.
Ongoing improvement
We constantly improve our data security processes as new technologies become available. Paying attention to data security not only shows our respondents they can trust us with their data, but it also ensures that the data we share with clients is accurate, reliable and contributes to high quality research.
Samuel Nzaramba is a Research Analyst at Laterite Rwanda.
